What's so tricky about Android security anyway
Monday, December 12, 2016

|
Don Duncan |
Android authentication can be a tricky business because it can help identify the user, but it can also open the door to hackers at the same time. It all comes down to the device administrator access which comes with a lot of benefits like.
Device administrator access provides complete device management access rights that include creating and managing policies, applications and configurations, usually involving advanced programmatic API access to the device. So vendors such as Google and Enterprise Mobility Management (EMM) solutions from IBM MaaS360, VMWare, MobileIron, Citrix and Samsung are typically used for the protection of corporate information on BYOD devices.
The vast number of applications found within the Google Play store does not require this level of access. If a recently downloaded application requires this level of access this should be red flag to users to abort the installation. It is precisely this level access that recent malware exploits have been using to gain device level access. Education is the best way to arm a corporate mobile user. Taking the time to download apps from known apps stores; not downloading from unknown sources; reading the reviews in the app stores; and checking with the corporate mobility team if there is any uncertainty are just some of the strategies that can be used to combat malware.
However, it is this level of access that also opens the door to malware and allows it to take control over a device pretending to be the user. This becomes a real risk when using a Bring-Your-Own-Device (BYOD) on the job where others can not only collect your personal information, but corporate data as well.
If a BYOD device is being used for both personal use and corporate work, then a MDM (Mobile Device Management) or EMM (Enterprise Mobility Management) solution should be provided by your employer to secure corporate information. Without this, there is no clear differentiation between corporate and personal data and it opens the potential for the device to be compromised by malware. Many solutions for BYOD devices now have access to a corporate application store with applications that have been reviewed and approved by their own internal IT and security teams.
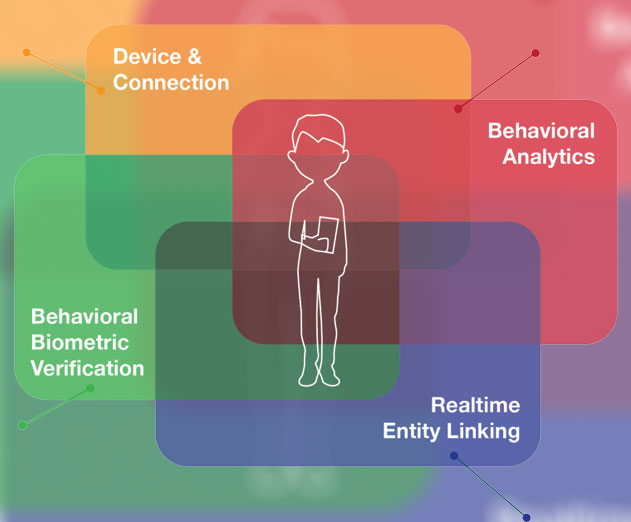
As behavioral biometrics has not found its way into being a component of mobile operating systems, NuData has been working with eCom and financial services institutions to bridge this gap by incorporating behavioral biometrics into their B2C applications as part of their Mobile First strategy. ECom and FinService organizations understand the pressing need to protect the customer from fraud, like malware automation, and are using behavioral biometrics to combat the after effects of these daily data breaches on the consumer side of a BYOD device. Application developers, especially those in the mobile space, have the means to devalue stolen credentials and combat fraudulent activity by looking at behavioral biometrics as the mechanism to determine whether it is an actual user on the device or a script impersonating one.
Which is Which?
There is a challenge with device authentication, as it assumes that the person with the device and the information on the device represents a living and breathing user and hopefully the one who is intended to use the device. Device authentication is a carry-over from the personal computing era which doesn’t map well to the new mobile world.
The days of one user to one device no longer exist; however, many of these security strategies have been carried over from that bygone era. Most users do not run anti-virus on their mobile devices; most don’t even think to do so. Those that are aware of this don’t run anti-virus because of the effect it has on their battery life. Also, many authentication solutions still have a reliance on using an ID/password and/or their device information to validate the user.
The concern is being able to effectively authenticate a mobile user without introducing latency in the form of time or frustration into the end user experience. Behavioral biometrics using a layered approach with multiple data points eliminates latency and friction. Taking many of the concepts from the business world, such as ‘know your customer’, allows application developers to understand whether they are dealing with a living breathing person or a form of automation masquerading as the user, or even a human bad actor. As no two people are alike, it is possible with behavioral biometrics to differentiate between the actual user and someone impersonating them eliminating the risk of being impersonated by hackers(s) or bad guys using information via the dark web obtained through data breaches.
Users have multiple devices in various forms, and it’s important in this age of the Internet of Things (IoT) to determine if there is a real user behind the device or if it’s an impersonator. For example; I may be driving the car, but that doesn’t mean it’s my name on the insurance slip in the glove box.
Will the Real User Please Stand Up?
The use of passive behavioral biometrics allows another level of authentication without introducing frustration into the user’s mobile experience. The use of passive behavioral biometrics during the user engagement is not only with the device, but the mobile application, and addresses many of the gaps in the existing mobile user authentication process making exploits much easier to spot. This is true when the device is being impersonated, or with malware, or when the data is farmed via intercepted SMS messages and later used for identity crimes.
Passive biometrics and behavioral analytics can detect if it’s the real human user interacting with the device or an imposter using the device. Hackers take over primarily at the user login, to initiate a transaction, credit applications, money movement, account changes, or opening new accounts. This enables corporations and financial organizations to make good risk decisioning at any of these stages because they have a fuller and more accurate understanding of the risk each user presents.
This content is made possible by a guest author, or sponsor; it is not written by and does not necessarily reflect the views of App Developer Magazine's editorial staff.

Become a subscriber of App Developer Magazine for just $5.99 a month and take advantage of all these perks.
MEMBERS GET ACCESS TO
- - Exclusive content from leaders in the industry
- - Q&A articles from industry leaders
- - Tips and tricks from the most successful developers weekly
- - Monthly issues, including all 90+ back-issues since 2012
- - Event discounts and early-bird signups
- - Gain insight from top achievers in the app store
- - Learn what tools to use, what SDK's to use, and more
Subscribe here